Data Security
CYCTEMS takes information and data security of our clients’, and its Stakeholders as its highest priority. Data information is our most important asset, and its security is our highest priority.
Our management takes overall responsibility to ensure that all our data is protected. Our management uses all appropriate, effective, and practical security measures to protect our important processes and assets to achieve our security objectives
Data Security
Protection against cyber threats
With strict security protocols in place, data security policies can help safeguard sensitive information against cyber threats such as hacking, malware, and phishing attacks.
Compliance with industry regulations
Data security policies can ensure compliance with industry regulations and standards, such as ISO 27001, HIPAA, GDPR, and PCI DSS. Compliance with these regulations not only helps avoid legal and financial penalties, but also builds trust with customers and stakeholders.
Enhanced reputation and customer trust
Effective data security policies can help build trust with customers and stakeholders by demonstrating a commitment to protecting their sensitive information. This can enhance the organization's reputation and increase customer loyalty.
Information Security
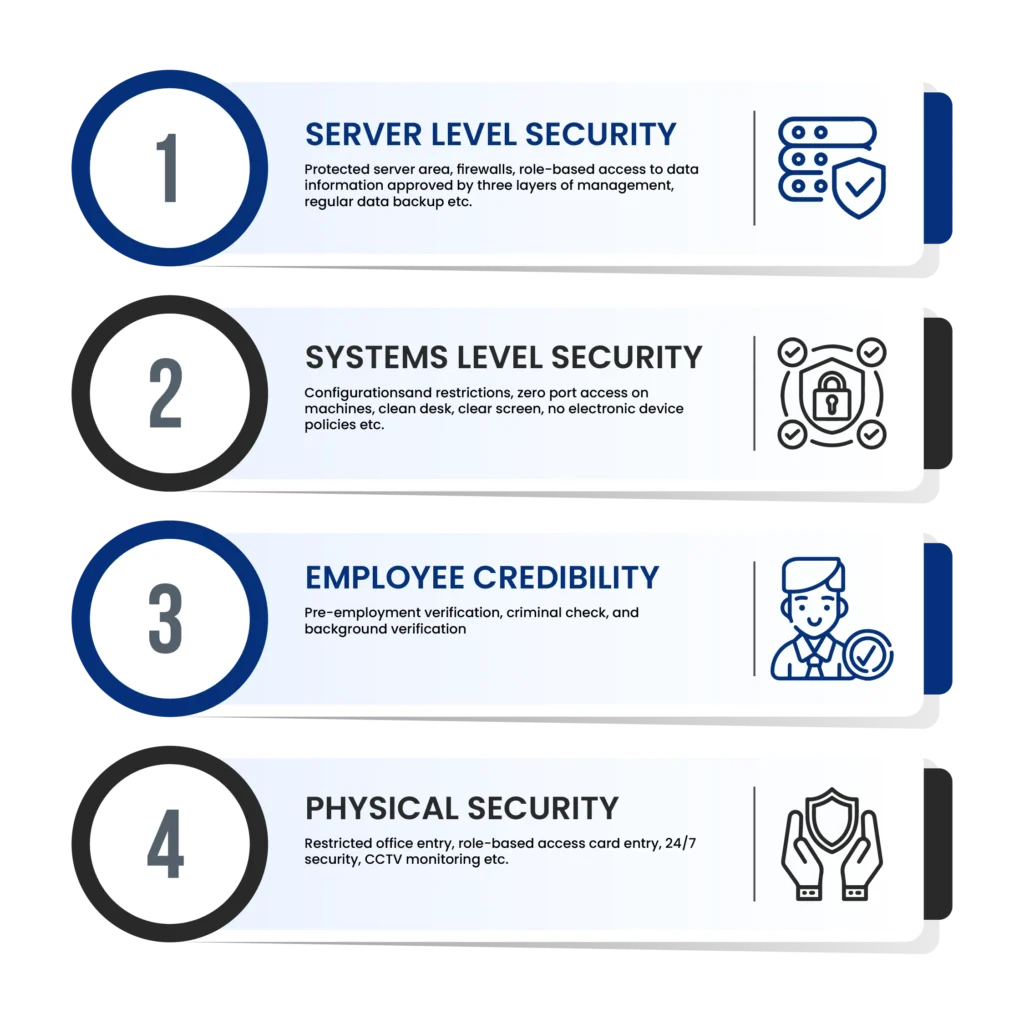
- SERVER LEVEL SECURITY (Restricted server area, firewalls, role-based access to data and information approved by three layers of management, continuous server data backup etc. policies)
- SYSTEM LEVEL SECURITY (Configurations and restrictions, zero port access on machines, clean desk, clear screen, no electronic device etc. policies)
- EMPLOYEE CREDIBILITY (Hired after pre- employment verification and signing of employment agreement covering non-disclosure agreement, confidentiality agreement and other protective clauses signed by employees).
- PHYSICAL SECURITY (Restricted office entry, role-based access card entry, 24/7 security, CCTV monitoring policies etc.)
- Server Level Security (Restricted server area, firewalls, role-based access to data and information approved by three layers of management, continuous server data backup etc. policies)
- Systems Level Security (Configurations and restrictions, zero port access on machines, clean desk, clear screen, no electronic device etc. policies)
- Employee Credibility (Pre-employment verification, criminal check, and background verification under HR policies)
- Physical Security (Restricted office entry, role-based access card entry, 24/7 security, CCTV monitoring policies etc.)

Through our security protocols, measures, internal policies, and procedures in place, we are committed to protect security of our client data. As a responsible organization, we protect and manage our data information to enable us to meet our contractual and ethical values along with industry compliances. Our ISMS data security protocols are audited and tested under annual ISO 27001 audit.
HOW WE ENSURE INFORMATION SECURITY
Annual Audits By Independent Agencies for ISO 9001 And ISO 27001 Certification | No Access To Personal Emails | Role Based Key Card Access Restrictions | Restriction To Social Media And Non-Work Related Websites | No Personal Notepads On Operations Floor |
|---|---|---|---|---|
Controlled And Limited Internet Access |
No Access To Printers |
DLP On All Machines |
Prohibited Personal Mobile Devices |
Multilayer Authentication |
Strong Fire Wall Protection |
24/7 CCTV Surveillance |
Role And Process Based access to Server |
Role And Process Based access to Process Information |
Disabled USB And Data Transfer Devices |